-
Products
- SAS - Singalarity Authentication Server & Token Management Server
- TAE - Troubleshooting Analytic Engine
- FSOC - Forensic Security Operations Center
- ST Engineering Data Diode - Secured Data Transfer Gateway
- Rnext - Business Management Platform
- Rnext - QRPay Intra-Gateway
- Rnext - Fintech Solution Platform
- Services
- Industries
- News & Analysis
- Opportunities
- About us
Best Practice: Improve Security Hygiene and Compliance through regular Host Security Review and Audit
Host Review is an important process in a security audit procedure, performing Host Review can give us an insight into our system and also provide useful information for conducting other security diagnostic actions.
Host Review is one of the mandatory steps taken to achieve the goals set out in the policy of an organization. Host Review is carried out in order to verify every hosts within the organization infrastructure are effective and suitable for achieving the stated goals.
For those systems of importance, a single misconfiguration could prove devastating, and by doing Host Review, we are making sure there are no loose ends from the inside of our system.
Overview of Host Review
Host Review is one part of the security audit procedure, the other is Vulnerability Assessment, Host Review is usually called “Host Audit” and can be defined as: “A systematic and independent examination to determine whether activities and related results comply with planned arrangements and whether these arrangements are implemented effectively and are suitable to achieve objectives.”
Figure 1. A Host Review could provide useful information about organization infrastructure and security posture.
A Host Review is carried out with the following objectives in mind:
● To evaluate whether the hosts in an organization infrastructure has followed security standards and guidelines.
● To offer opportunity to improve security posture, maintain system stability.
● To provide an insight of an organization system, and provide more information for the security audit procedure.
● To determine conformity or nonconformity of the system elements with the specified requirements to assure the system can go live.
A Host Review usually covers:
● OS versions & patching: ensure the host under review is up-to-date with the latest security patch and hotfixes to reduce as many vulnerabilities as possible and provide more stability of the machine.
● Local Firewall Configuration: accept trusted connections and reject or drop external and suspicious connections; also firewall can log all attempts to enter private network or an individual computer and set an alarm (in the form of a pop-up or other notice) when suspicious or hostile activity is attempted.
● Control Access: only the right personnel with the right token has access to the host.
● Logging: record actions that have been taken by whom to help improve security in a variety of ways such as intrusion detects, system health monitoring…
The targets of a host review could be Web Server, Application Server,
or Database Servers.
Performing Host Review
The process of Host Review can be divided into 3 main phases: Gather and Preparation, Test and Review Results, and Analysis, Mitigations and Recommendations
Gather and Preparation
This phase could be divided further into 3 sub steps. In this step, the auditing team spends various interview sessions with stakeholders to understand their system infrastructure, walkthrough to the demo session to understand how to setup scan parameters and profiles, and further sessions to understand the adopted policies, guidelines and the environment they provide for host review.
● Walkthrough and Interview Session: the auditing team will be looking at various documents describing the system infrastructure such as design specifications, illustrative diagram, and even the workflow of the system, to better grasp the infrastructure. Moreover, the auditing team nay hold an interview with the client team to collect information about how each host is built and configured.
● Standards for Host Review: the auditing team and client will agreed on the suitable guidelines and standards used for this work, it will be defined in the report that will be given to the client later. Example of agreed guidelines and standards used in our client system is shown below.
● Test machines, Environment and Server: we will be preparing a provisioned laptop with specifically approved OS by our client. Depending on the clients, this may be optional, if our client servers are very important or belong to the governments, this will be compulsory since we don’t want anything wrong to happen. All necessary information regarding the environment (usernames, passwords, location of servers…) and the servers themselves will be provided to make sure the process will be smooth and accurate. Then the works will be carried upon all hosts in their infrastructure against the prepared standard checklist.
Figure 2. Sample of a list of guidelines and standards that will be used for Host Review
Test and Review Results
The process may take about 2 to 4 days depending on the amount of audit items (based on the agreed standards) and the number of servers to be reviewed. This is done by either using the scripts may especially for auditing or do it manually for some items require human attention (such as legacy items) or additional requirements from our clients that is not belong to any agreed standards.
After the testing process is done, the auditors will be checking the values of the audited hosts against the items in the checklist, the review process is done two times, in which the first time will be by two different personnel with the role of Quality Control to ensure the audited items match with the guided items; the second time will be by technical team who will then doing the Pass/Fail verification.
Finally, we will provide our client with the Host Review reports (HR
reports) for each hosts, the client-side now just need to rectify any items
with the “Fail” status.
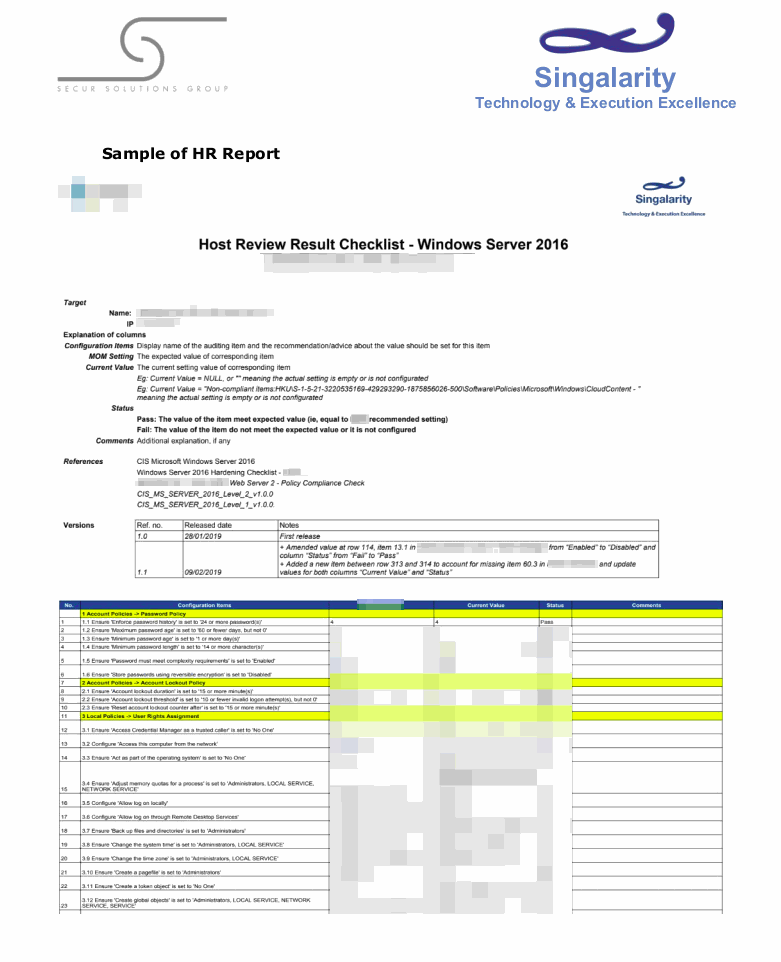
Figure 3. Sample of a HR Report of a Web Server that runs Windows Server 2016
Analysis, Mitigations and Recommendations
At this stage, the Host Review is coming to an end, along with Vulnerability Assessment. The final report consists of procedure and testing methods for both Host Review and Vulnerability Assessment. Our security analysis expert will provide insight to the problems we have discovered and give advice to remediate them.
In summary, Host Review is an important asset of security audit, it
ensures the overall security and stability of hosts in the system
infrastructure which in time boost the reliability of the system.
Share: