-
Products
- SAS - Singalarity Authentication Server & Token Management Server
- TAE - Troubleshooting Analytic Engine
- FSOC - Forensic Security Operations Center
- ST Engineering Data Diode - Secured Data Transfer Gateway
- Rnext - Business Management Platform
- Rnext - QRPay Intra-Gateway
- Rnext - Fintech Solution Platform
- Services
- Industries
- News & Analysis
- Opportunities
- About us
Vulnerability assessment - The first step in securing your business from cybersecurity threats
With the constant rise of cybersecurity threats, organizations are at risk of being targeted by unknown attackers on the Internet through infinite ways. This blog will give us an insight on how vulnerability assessments can help to identify and solve the security problems in our infrastructure.
The trend of cybersecurity risks is rising and any organization can be the target of an exploitation or data breach, which can result in loss of data and compromising customers’ personal and bank account information, eroding customers’ confidence and trust. The following graph shows us how rapidly cybersecurity threats have grown.

Figure 1. Bar Graph of Global number of Security Incidents from 2009 to 2015
As can be seen from this graph, the number of cybersecurity incidents in the world has increased steadily and experienced a sharp rise from 2014 to 2015. This trend is expected to accelerate in the coming years, with a record high cyber incidents occurring in 2017.
These exploits could have been prevented if organizations have taken adequate precautions and preparations to face them seriously. It’s never too late to prepare. One crucial element of security diagnostics that will help us identify the areas that need to be reinforced against cyber threats is to conduct a Vulnerability Assessment.
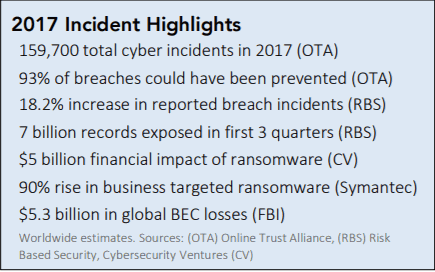

Figure 1. Bar Graph of Global number of Security Incidents from 2009 to 2015
As can be seen from this graph, the number of cybersecurity incidents in the world has increased steadily and experienced a sharp rise from 2014 to 2015. This trend is expected to accelerate in the coming years, with a record high cyber incidents occurring in 2017.
These exploits could have been prevented if organizations have taken adequate precautions and preparations to face them seriously. It’s never too late to prepare. One crucial element of security diagnostics that will help us identify the areas that need to be reinforced against cyber threats is to conduct a Vulnerability Assessment.

Figure 2. Cybersecurity Incident Highlight in 2017 (source: Ponemon Institute and IBM)
Vulnerability Assessment Overview
First, we need to define what a “vulnerability” is. As documented by SANS (Escal Institute of Advanced Technologies), “Vulnerabilities are the gateways by which threats are manifested”. In other words, they are weaknesses found in a system which, when exploited, can allow attackers to non-permissible access to the system.
A Vulnerability Assessment is a systematic approach
So, where do these weaknesses occur? There are two points to consider:
Many systems are shipped with: known and unknown security holes and bugs (from software, or from vendors…) and insecure default configurations (weak passwords, account policies…).
Vulnerabilities as a result of misconfigurations by
system administrator (read more about itat: OWASP A5).
Why should we perform Vulnerabilities Assessment?
The main reason why we should maintain security awareness of vulnerabilities in organizations’ environment is to quickly mitigate potential risks. A Vulnerability Assessment can be done prior to product deployment or after - the earlier, the better, to identify security holes in the system and fix them, before attackers have any opportunity to exploit or damage the system.Additionally, ensuring a high level of cybersecurity is often part of strict requirements in large companies or government agencies, which a Vulnerability Assessment can help to achieve and evaluate, for example, for the following security requirement:

Figure 3. Example of a security requirement of a government system
Through a thorough Vulnerability Assessment, we can evaluate whether the system has been set up to comply with the aforementioned requirements, and of not, take immediate action to apply remediation.
Last but not least, a Vulnerability Assessment is done to make sure the system is compliant with the new data security and data privacy laws across the world such as the Cybersecurity Law in Vietnam that will take effect on 01/01/2019.
Vulnerability Assessment Process
Our method of conducting Vulnerability Assessment consists of 4 steps, which can effectively identify vulnerabilities most organizations have:
1. Reconnaissance
We will identify, analyse and map out the assets of the organization, including devices, their placement, network topology, and the importance of the devices to the IT infrastructure and network. This will provide a comprehensive overview of the IT assets in the organization.
2. System Information Gathering
Second, we will gather information about the systems before starting the Vulnerability Scanning. We will be review the ports, processes, services, and policies in the system to check for any misconfiguration that needs to be fixed. We will also require credentials of those devices to ensure the optimal performance of the Vulnerability Scanning.
3. Perform Vulnerability Scanning
In this step, we will use the information acquired from the previous steps to configure our proprietary scanner and then proceed to scan the system. The scan is divided into two types: external and internal.
External Scan will simulate how an attacker from outside your organization see and attempt to exploit the system.
Internal Scan, also known as scanning with credentials, will attempt to log on to each host on your network and collect additional detailed information about the host while it performs comprehensive vulnerability checks inside your network. Common checks include security updates, policy check, encryption
and authentication…
Our Vulnerability Scanning follows many security standards and configurations (see below) that are guaranteed to produce desirable results.
- National Institute of Standards and Technology (NIST)
- Common Vulnerabilities and Exposures (CVE)
- Open Web Application Security Project (OWASP) Top 10
- Firewall Scan
- Full Port Scan
4. Summary Report
The final and most important step of the Vulnerability Assessment is the actual detection of vulnerabilities. This is done by utilizing a detection tool or vulnerability repository list in the previous step to identify the vulnerabilities on the assets listed earlier. This process generates reports, complete with scores and risk information. The final step of the phase is to use remediation tools to patch, configure, or debug assets to reduce or eliminate the security risks present from the vulnerabilities detected.
Here is an example of a risk we identified in our report:
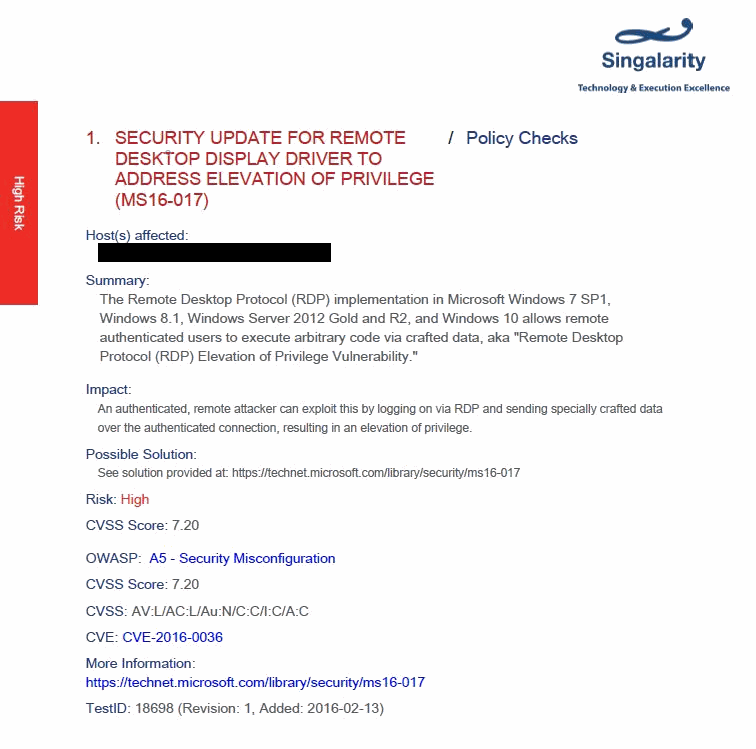

Figure 4. Example of a vulnerability assessment report, which identifies the risk and scoring information for better understanding, and recommended solution to remediate the risk.
For organizations seeking to reduce their security risk, a Vulnerability Assessment is a good place to start. It provides a thorough, inclusive assessment of hardware and software assets, identifying vulnerabilities, providing an intuitive risk score, and solutions to remediate the vulnerabilities. A regular assessment program helps organizations to manage their risk in the face of an ever-evolving threat environment, identifying and scoring vulnerabilities so that attackers do not catch organizations unprepared.
Share:

