-
Products
- SAS - Singalarity Authentication Server & Token Management Server
- TAE - Troubleshooting Analytic Engine
- FSOC - Forensic Security Operations Center
- ST Engineering Data Diode - Secured Data Transfer Gateway
- Rnext - Business Management Platform
- Rnext - QRPay Intra-Gateway
- Rnext - Fintech Solution Platform
- Services
- Industries
- News & Analysis
- Opportunities
- About us
Penetration testing - The key step to securing your business from cybersecurity threats
Penetration Testing can contribute a lot to an organization's security by helping to identify potential weaknesses. But for it to be truly valuable, it needs to happen in the context of the business. This article will provide the overall knowledge and preparation for conducting a proper Penetration Test, how Penetration Testing is carried out to maintaining the security posture of our organization
With the advancement of technology, almost every organization of all sizes have a network presence, and the Internet has made it easy for attackers to target organizations around the world. A cyber attack could be devastating and cause tremendous damage to an organization in many ways, not just in terms of direct financial impact, but also their reputation, brand, and intellectual property.
A penetration test, as a necessary supplement to security audit and vulnerability assessment, can help organizations build a more robust and reliable security infrastructure and significantly reduce the surface/chance that they will be targeted by attackers.
What is Penetration Testing?
A Penetration Test, also known as pentest , is the authorized process of simulating real cyber attacks against an IT asset such as IT system, infrastructure or software applications like web or mobile applications. The purpose of doing a Penetration Test is to uncover exploitable vulnerabilities, assess the risk associated with potential security breaches, and address them before anybody else exploits the vulnerability.
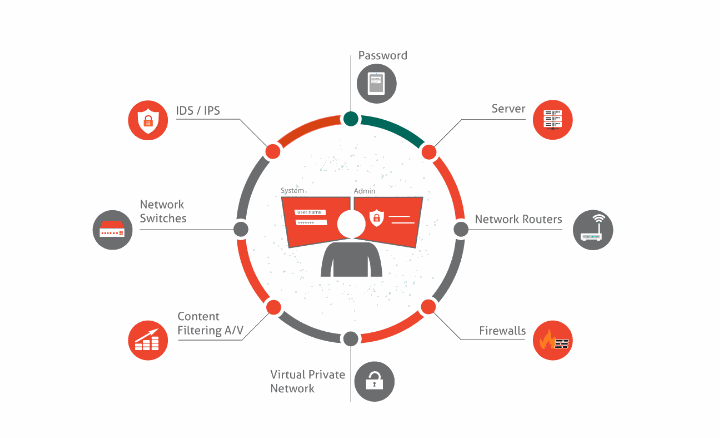
Figure 1. Common Items are that are usually assessed in a Penetration Testing (source: SourcetekIT)
What distinguishes a penetration test from an attack is that permission has been granted and the penetration conducted is not malicious. A penetration tester (pentester) will have permission from the organization to conduct the test on the IT system and will be responsible for providing a post-hoc analysis report detailing how the test was carried out and the test findings, whereas an attacker targets the IT system and maliciously exploits any vulnerability found without permission for the benefit of the attacker.
Benefits of performing Penetration Testing
A Penetration Test utilizes the techniques that are used by hackers to get into the targeted system to simulate a real-case scenario. This provides the following benefits:
+ It identifies your vulnerabilities before real attackers could identify and exploit them. A pentest will provide extensive information about the vulnerabilities so organizations can take preemptive action to rectify them before it becomes a threat.
+ It gives an overview of vulnerabilities based on their exploitability and impact, so organizations can prioritize the risks of these vulnerabilities, and plan their remediation efforts accordingly.
+ It helps your organization comply with industry standards and regulations, such as ISO 27001, NIST, FISMA, HIPAA, Sarbanes-Oxley or the Payment Card Industry Data Security Standard (PCI DSS), which requires annual and ongoing penetration testing (in cases of system changes).
+ It gives an overview of vulnerabilities based on their exploitability and impact, so organizations can prioritize the risks of these vulnerabilities, and plan their remediation efforts accordingly.
+ It helps your organization comply with industry standards and regulations, such as ISO 27001, NIST, FISMA, HIPAA, Sarbanes-Oxley or the Payment Card Industry Data Security Standard (PCI DSS), which requires annual and ongoing penetration testing (in cases of system changes).
+ It keeps the executive and security team informed about the overall health of your organization.
What to prepare before conducting a Penetration Testing
Some organizations feel they need to perform pentest because they have to comply with regulations, satisfy auditors, or because the board of directors asks for it, even when they do not see the need for pentest . To secure buy-in within the organization, planning ahead to make sure the pentest produces a useful result is necessary. To do so, the organization should:
+ Dedicate appropriate time and budget for the test
+ Dedicate appropriate time and budget for the test
+ Clarify the proper scope of work, what are target IT systems or assets to be tested, what key findings are expected from the pentest outcome
+ Understand what types of pentest is needed
+ Understand when to do it - run regularly/annually to maintain the security posture, or to check new systems before they go into production
+ Finally, dedicate engineering resources to fix or mitigate vulnerabilities found during the pentest
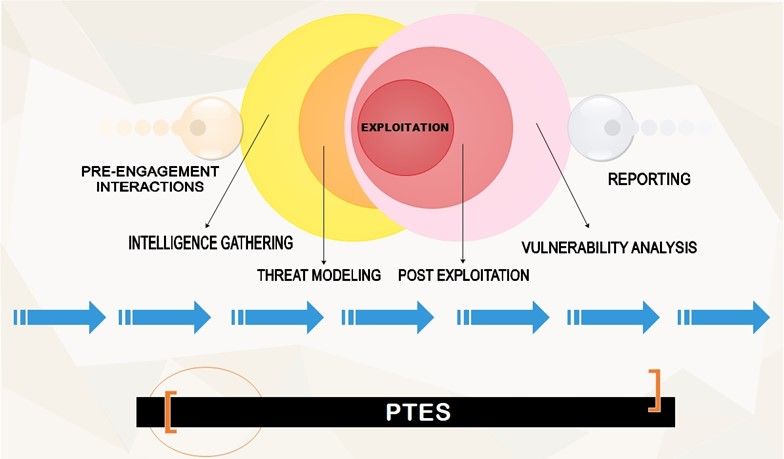
Figure 2. The Penetration Testing Execution Standards (source: infosec)
Adequate preparation not only saves time and money but also guarantee the test will give the useful and actionable results.
Types of Penetration Testing
The type of penetration testing to be conducted depends on the scope and requirements in the pre-engagement step. In general, there are three types of pentesting: Black Box Pentest, White Box Pentest and Gray Box Pentest:
Black Box Pentest
In black box penetration test, the tester has no knowledge of the target that he is going to test. This type is considered external test since pentesters have no information about the system, they will use various information gathering techniques and skills such as social-engineering and analysis to perform the attack. This is often used to simulate what an outside attacker could accomplish when targeting a system. Black box pentest often takes a lot of time and requires more resources compared with the other two pentests.
White Box Pentest
In white box penetration test, the tester has full knowledge of the internal structure of the organization’s system, their network infrastructure, source codes, and their applications. This pentest is opposite from black box penetration test. This type of test is also called a glass box test due to the full visibility that the testers will have. The pentesters will not need to perform information gathering since most of this information is provided, which will allow them to perform a comprehensive attack and easily discover vulnerabilities, configuration flaws and loopholes based on the source codes, and diagrams that have been provided. This is often used to simulate an attack from inside the organization - from a disgruntled employee or an outside attacker who has already gained access to the foothold in the target.
Grey Box Pentest
In grey box penetration test, tester has partial knowledge of the system that he is going to attack, which is somewhat between a black box and white box penetration test. Pentesters are given credentials, application flows, network architecture and diagrams to conduct the penetration test. However, they won’t have full knowledge of the scope such as the inner workings of the system (e.g. applications used, versions). The pentesters also performs information gathering and scanning before performing the attack. This is often used to simulate an attack that is done by an outside attacker who had gained knowledge of an organization’s network infrastructure document and access to their employee accounts.
Penetration Testing vs. Vulnerability Assessment
Many people are usually confused about the differences between Penetration Testing and Vulnerability Assessment.
In our previous blog post, we have noted that Vulnerability Assessment is a systematic approach of identifying, quantifying, and ranking vulnerabilities with the combination of automated and manual scan. It is a non-intrusive approach aiming to produce a prioritized list of security vulnerabilities of one organization.
Penetration testing, on the other hand, is an attempt to exploit identified security weaknesses to gain access into the IT infrastructure and applications of the organization. It is an intrusive approach to exploit the security weaknesses in the organization.
The difference between vulnerability assessment and penetration testing is that the former helps us discover and list security vulnerabilities in organization's system but does not exploit them. The latter goes as far as possible within the scope of contract to demonstrate how dangerous security vulnerabilities are in a real cyber attack. Although these two approaches serve different purposes, they are often used together to provide a comprehensive picture of the security loopholes that exist in the IT system and infrastructure, and how they will be affected.
Comparison Table between Penetration Testing and Vulnerability Assessment
| Vulnerability Assessment | Penetration Testing | |
| Attributes | List-oriented | Goal-oriented |
| Types of Reports | Specific information of what data was compromised and vulnerabilities exploited | |
| Purpose | Identify security vulnerabilities in a system that may be exploited | Determine whether a system can withstand an intrusion attempt |
Stages of Penetration Testing
Our services adhere to the Penetration Testing Execution Standards and we have divided our penetration testing procedure into 7 steps as shown below:

The first step is Pre-engagement, which is the step taken before the pentest begin. In this step, we will engage with our clients to ensure that everyone is aligned towards the same goals for the pentest . This stage is when we ask and gather requirements from our client, such as the scope of pentesting (what actions are allowed and/or not allowed, what types of penetration testing our client wants), contact information (who to inform when we encounter something serious), etc. Finally, we will include a nondisclosure agreement clause in our contract to keep the penetration test and any findings confidential.
The second step is Information Gathering, to look into available sources of information, also known as gathering open source intelligence (OSINT), we will start searching around on the Internet to have a gist on what information is published out there on the Internet, and using tools such as port scanners to identify internal systems.
The third step is Threat Modeling, which will make use of the information we have gathered on the two previous phases to devise plans of attack. This will allow us to simulate a real cyber attack. For example, if the client is running a healthcare service, attacking to the web application where personal data is received for registration could affect the client greatly, such as theft of patients’ information, which could be modified and used for malicious purposes (identity theft).
The fourth step is Vulnerability Analysis , when we actively interact with the client system so that we can identify as many vulnerabilities as possible. This stage includes using scanning tools to list vulnerabilities that are present in our client’s system. We then perform manual analysis (where we pass various inputs to the application and record responses) to verify the vulnerabilities (such as injection, remote code execution) identified. Now we are ready to exploit.
The fifth step is Exploitation , when we attempt to access the client’s systems by using various tools against the vulnerabilities we have discovered.
The sixth step is Post-Exploitation , when the pentests truly begin to answer the questions “What next?”, “Does it mean much for the client if we have broken into an unpatched legacy system that isn’t a main part of a domain?”, “Does it mean much if we cannot prove how damaging it can be if attackers could gain access to our client’s system?”, “So what next after we have exploited the system successfully?” This is the step where we look around our client’s systems for interesting files, attempt to access where sensitive files are stored by escalating our privileges etc. We might also dump password hashes to attempt to access other machines/systems or launch an DOS attack to other parts of the system. Based on the scope defined in the pre-engagement step, we may restrict our action against sensitive and fragile system (SCADA for example), which can be done by placing a dummy flag in the critical zones (in database server, OPC server), so that any simulated attack will avoid the parts that have been designated as out-of-scope.
The final step is Reporting , when we will convey our findings to our client. A comprehensive report will include what our client is doing correctly and what need to be done to improve the security posture, depict the pathways in which we successfully exploited the system, what information we have found, and most importantly, solutions to resolve the identified vulnerabilities.
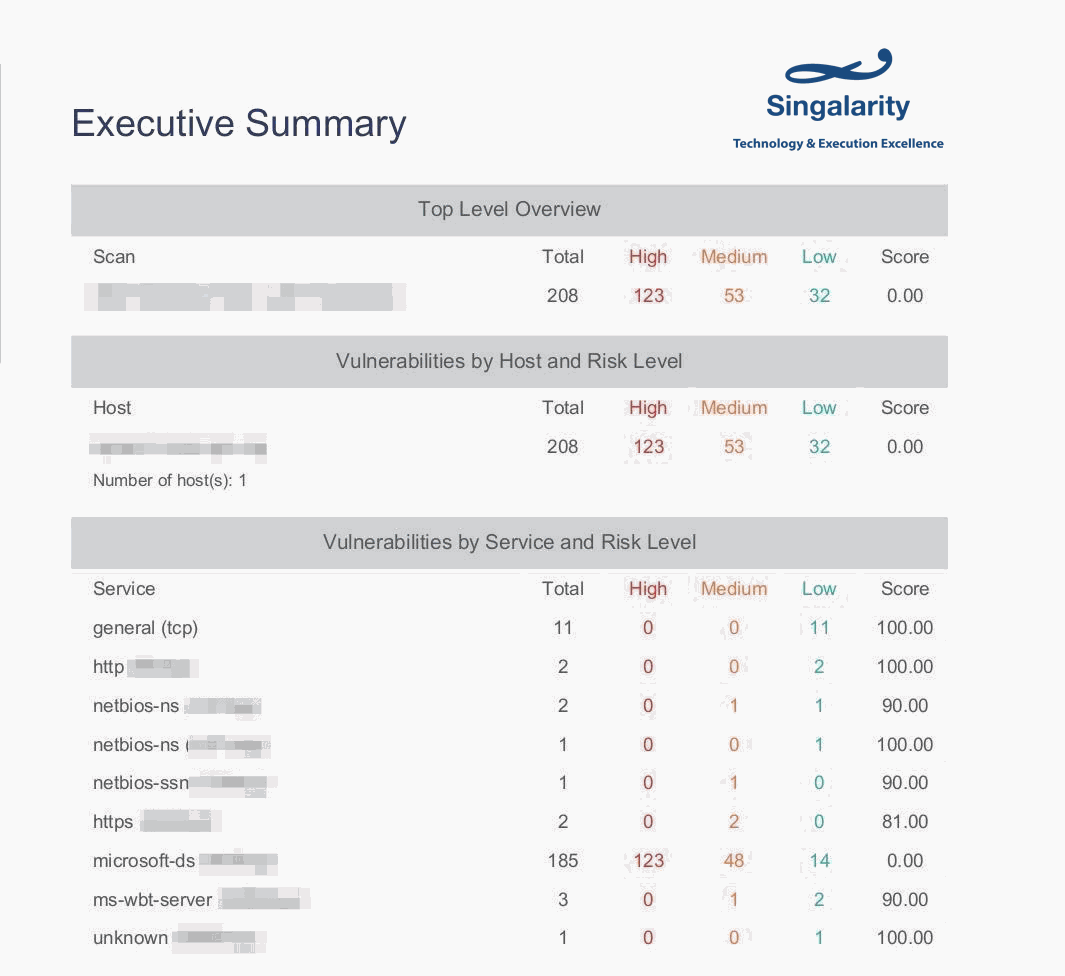

Figure 3. An example of our conducted vulnerability analysis, it shows the ports and their vulnerabilities of our client.
In conclusion, Penetration Testing should not be overlooked, as it could help your organization prioritize risks that need to be remediated first, and save time dealing with security problems after they have occured . It also provides an in-depth analysis of your security posture, and provide ways to secure it before the attackers have a chance to exploit the vulnerabilities. Combining with Security Audit and Vulnerability Assessment, they will keep your organization’s assets healthy and secured .
Share:

